Candybowl
Candybowl
Challenge
- CTF: Hack The Boo 2023 - Practice Official Writeup
- Name: Candybowl
- Category: Reversing
- Difficulty: Very Easy
- Points: 300
- Description: Dip your hand in my candy bowl and see if you can pull out a flag!
- Objective: Strings
Files
Download: rev_candybowl.zip
Writeup
The challenge contains a single file of candbowl. Analyzing using the file utility, we see its a Linux ELF binary.
1
2
file *
candybowl: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=30c0582cde593ca34da52bc9919191f64b7bf0fa, for GNU/Linux 3.2.0, not stripped
Running the binary, we are shown it selects a random candy.
1
2
3
4
5
6
./candybowl
Reaching into the candy bowl...
Your candy is... 'Take 5'. Enjoy!
./candybowl
Reaching into the candy bowl...
Your candy is... 'Warheads'. Enjoy!
We can use dogbolt or ghidra to reverse the binary back to C as shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
int main(void)
{
int iVar1;
time_t tVar2;
tVar2 = time((time_t *)0x0);
srand((uint)tVar2);
puts("Reaching into the candy bowl...");
sleep(3);
iVar1 = rand();
printf("Your candy is... \'%s\'. Enjoy!\n",
*(char **)(candy + (long)(iVar1 + (int)((ulong)(long)iVar1 / 0xd1) * -0xd1) * 8));
return 0;
}
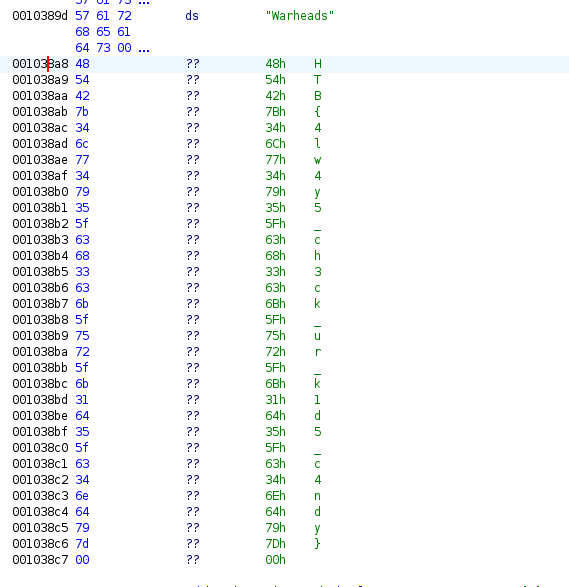
We can also find the flag within the binary using Ghidra. This is stored in close proximity to where the candy strings are:
We can also find the flag by doing a simple string-grep search:
1
2
strings candybowl | grep HTB
HTB{4lw4y5_ch3ck_ur_k1d5_c4ndy}
Flag: HTB{4lw4y5_ch3ck_ur_k1d5_c4ndy}
This post is licensed under CC BY 4.0 by the author.